This topic explains how to enable scripting in Windows PowerShell, which script extensions are used in Windows PowerShell, how to enable running PowerShell scripts, how to create a script and how run a script.
Enabling Windows PowerShell Scripts to Run
When you start Windows PowerShell on a computer, the default security policy does not allow you to run scripts. The Windows PowerShell security policy for scripting is called an execution policy. The execution policy lets you determine whether scripts can run in your environment and whether they must include a digital signature. None of the execution policies in Windows PowerShell allow you to run a script by double-clicking its icon because that is a high-risk method of running a script.
The following execution policies govern scripting in Windows PowerShell:
- Restricted. Permits interactive commands only (no scripts). This is the default.
- AllSigned. Permits scripts, but requires a digital signature from a trusted publisher for all scripts and configuration files, including scripts that you write on the local computer.
- RemoteSigned. Permits scripts, but requires a digital signature from a trusted publisher for all scripts and configuration files that are downloaded from the Internet, including e-mail. A digital signature is not required for scripts that you create on the local computer.
- Unrestricted. Permits scripts, including unsigned scripts.
Because the default Windows PowerShell execution policy is Restricted, you cannot run Windows PowerShell scripts until you change to a less restrictive execution policy. The following table lists Windows PowerShell Help topics that explain what you need to know about Windows PowerShell execution policies and how to change your policy so that you can run scripts.
To get information about Windows PowerShell execution policies
| Type at the command prompt | Description |
|---|---|
|
Displays information about Windows PowerShell execution policies and the levels of security that the execution policies provide. |
|
|
Displays information that explains how to determine your current scripting security policy. |
|
|
Displays information that explains how to change your scripting security policy. |
Identifying Windows PowerShell Script Extensions
Three extensions are available for script files in Windows PowerShell, although most script files have the .ps1 extension.
Windows PowerShell script extensions
| File type | Extension | Description |
|---|---|---|
|
Windows PowerShell script |
.ps1 |
A standard Windows PowerShell script. |
|
Windows PowerShell console file |
.psc1 |
A special type of script file that defines the configuration of a specific Windows PowerShell console. For example:
For more information about Windows PowerShell console files, type Get-Help Export-Console at the command prompt. |
|
Windows PowerShell format and type definitions |
.ps1xml |
A type of script file that provides a mechanism for extending the Microsoft .NET Framework type system. These script files are in the Windows PowerShell home directory (<C>:WINDOWSSysWOW64Windowspowershellv1.0), For more information, type Get-Help about_Types at the command prompt. |
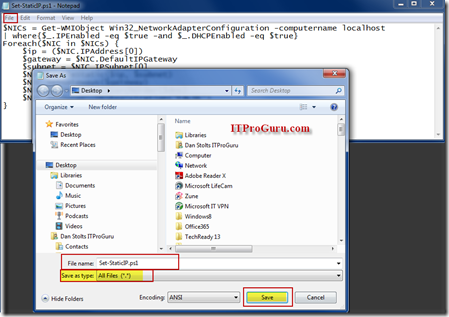
Creating a PowerShell Script
A PowerShell script is nothing more than a TEXT file. You can create it with notepad or any other text editor. When you save it give it a .PS1 extension. If you have extensions hidden, you will need to select file type All Files (*.*)
Running a Windows PowerShell Script
When you run a Windows PowerShell script, you must always indicate the full path with the name of the script even if you are working in the directory in which the script is located. If the script needs (or powershell command window) needs elevated permissions to do a task you will get an error if you have not run the PowerShell window using elevated permissions. See How to Run Any Program Including PowerShell with Elevated Privileges (aka Administrator Permissions). You can use the following methods to run a Windows PowerShell script:
- Use the dot and the backslash (.) to indicate the local directory. For example:. <ScriptName>.ps1
- Specify the full path of the script. For example:C:Scripts<ScriptName>.ps1
- Specify the path of the script, but omit the extension. For example:C:Scripts<ScriptName>
- Use the Invoke-Expressioncmdlet to run a script. For example:Invoke-Expression C:Scripts<ScriptName>.ps1
- Use double quotation marks for any paths that include spaces. For example:Invoke-Expression “C:My Scripts<ScriptName>.ps1”
- Use the ampersand to run a script. For example:& C:Scripts<ScriptName>.ps1
Enable Policy to Allow Scripts To Run – Set ExecutionPolicy
In order to run a script, you have to allow that script to run. I will do this by setting my execution policy to RemoteSigned.
RemoteSigned – Scripts can run. – Requires a digital signature from a trusted publisher on scripts and configuration files that are downloaded from the Internet (including e-mail and instant messaging programs). – Does not require digital signatures on scripts that you have run and that you have written on the local computer (not downloaded from the Internet). – Risks running unsigned scripts from sources other than the Internet and signed, but malicious, scripts. See http://technet.microsoft.com/en-us/library/dd347641.aspx for more detail.
first I want to get the current execution policy
get-executionpolicy -list
Scope ExecutionPolicy
————- —————
MachinePolicy Undefined
UserPolicy Undefined
Process Undefined
CurrentUser Undefined
LocalMachine Undefined
There are no policies defined which means it is using the default which is Restricted.
Restricted – Default execution policy. – Permits individual commands, but will not run scripts. – Prevents running of all script files, including formatting and configuration files (.ps1xml), module script files (.psm1), and Windows PowerShell profiles (.ps1).
You can change the policy by issuing the PowerShell command. But that does not work. It does not work because you likely do not have the rights to change this setting. However, when you run the command you do get a pretty detailed error message.
Set-ExecutionPolicy RemoteSigned
NOTE: if you try to set the ExecutionPolicy from a PowerShell window (even if it has elevated privileges) you will get a message similar to:
Set-ExecutionPolicy : Access to the registry key ‘HKEY_LOCAL_MACHINESOFTWAREMicrosoftPowerShell1ShellIdsMicrosoft
.PowerShell’ is denied.
At line:1 char:20
+ Set-ExecutionPolicy <<<< RemoteSigned
+ CategoryInfo : NotSpecified: (:) [Set-ExecutionPolicy], UnauthorizedAccessException
+ FullyQualifiedErrorId : System.UnauthorizedAccessException,Microsoft.PowerShell.Commands.SetExecutionPolicyComma
nd
The only way I see to get around this is to manually go into the registry to set the settings.
WAIT – You know what they say about editing the registry – Perform this task at your own RISK!
Start – regedit – <ENTER>… drill down to the proper location…
Expand:
- HKEY_LOCAL_MACHINE
- SOFTWARE
- Microsoft
- PowerShell
- 1
- ShellIds
- Microsoft.PowerShell
If there is an ExecutionPolicy value in the right pane, just change it to RemoteSigned (Double-Click). If there is not, you will have to create a String Value.
- Right-Click
- New
- String Value
- type ExecutionPolicy
- Double-Click on ExecutionPolicyto edit
- Type RemoteSigned
- Click OK
Once you do this, you can run the get-executionpolicy –list command again with the following results
Scope ExecutionPolicy
—————- —————
MachinePolicy Undefined
UserPolicy Undefined
Process Undefined
CurrentUser Undefined
LocalMachine RemoteSigned
Now you can run PowerShell scripts on your local machine!
Related Articles:
How to Run Any Program Including PowerShell with Elevated Privileges (aka Administrator Permissions)
Other References: Running Scripts